Solutions
What is DNS RPZ?
Filter and block known bad domains at the DNS level.
Threat Intelligence on known malicious sites (malware, ransomware, bots, etc) is packaged into Data Zones that are consumed by a DNS resolver to block access to known malicious sources on the internet. Fast, timely updates (every 1 minute) enable an advanced layer of protection for all users, all applications, and all protocols.
A highly-effective and critical choke point against ongoing attacks such as ransomware, and malware, RPZ blocks both incoming and outgoing malicious sources from entering a network.
Turn your DNS Caching Resolver into a tool to help protect your network from malware, ransomware, phishing.
- Critical Choke Point – Any user, Any protocol, any Application using the Internet will use DNS.
- Stop connections to known bad domains on the Internet. Period.
- Elegant way to deploy dynamic threat intelligence
- Customizable and granular zones
- Highly dynamic.
- Fast accurate up to date Threat Data
- Timely updates – every 120 seconds
- Clientless
- Secondary layer of security at DNS level !
Solutions
How does DNS RPZ Work?
Filter and block known bad domains at the DNS level.
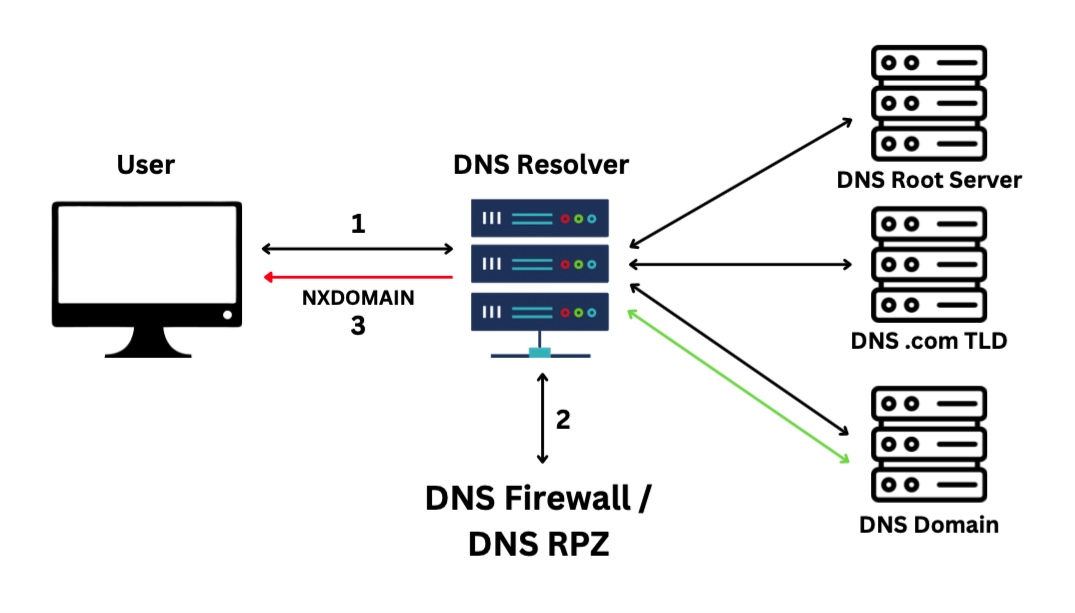
RPZ implements real-time threat intelligence domain data at the DNS level. DNS resolvers utilize RPZ data to protect users trying to visit known bad domains.
- User submits a request to the DNS Resolver.
- DNS Resolver queries the Response Policy Zone feeds to assess if the domain or related IP address is a known malicious threat.
- If domain being queried is malicious, the DNS Resolver will be re-directed to stop the user from accessing the bad domain. Blocked domains will be re-directed to “NXDOMAIN” or a defined modified value.
- If the domain is not listed in the RPZ feeds, then DNS request will resolve
DNS RPZ
- Add DNS RPZ data from Spamhaus and SURBL BV directly into your DNS resolver
- Continuous updates every 1-2 minutes, 24x7x365
- No updates to end users, or devices
- protects every user, application and protocol in your network
everyone and everything that uses the internet
When users attempt to access websites a five-step process takes place:
- User clicks on a link or enters the URL of the site they want to reach into their browser.
- A DNS resolver queries the local DNS server for a record.
- The DNS server finds a matching IP address. The Berkeley Internet Name Domain (BIND) is a popular open-source software used to translate domain names into IP addresses.
- The DNS server returns the IP address to the DNS resolver.
- The user’s web browser now contacts the website using its IP address.
- ISP’s
- Hosting Providers
- Enterprises
- Universaties
RPZ can easily be implemented on many open-source DNS platforms… BIND v9.8+ has native support for RPZ
Easily added to most DNS resolver / appliances
All of the devices in your network must contact your DNS resolvers to reach the outside world, and the DNS RPZ uses secure and fast zone transfer technologies to put a domain blacklist into your DNS resolver. The data on this list is automatically updated every 1 to 2 minutes, ensuring that you have access to the most up-to-date information to prevent users from visiting known malicious domains, including newly registered domains and known bad IP addresses, keeping your business and your customers protected.
The DNS response policy zone (RPZ), also known as a DNS firewall, blocks the resolution of known, malicious domains at the DNS resolver/lookup. The DNS RPZ starts with a filter to check if the domain is known to be malicious and if it’s a known bad website. Then the DNS RPZ protects users from visiting that site with warning messages, blocking, and quarantine. This turns your DNS caching resolver into a tool that helps protect your network from malware, bots, spyware, and other cyber threats.
The DNS RPZ is similar to an anti-spam DNSRBL, but offers greater degrees of scaling and speed. This highly dynamic and customizable tool offers a critical choke point to prevent users from accessing known malicious websites. The DNS RPZ also helps to prevent data loss by disrupting communications between C&C servers and infected botnet nodes on your network.
- Improved protection for users !
- Fast, up to date coverage against new/current threats
– Malware, phishing, ransomware - Network based, agent less, security – ease of updates, up to date protection
- Identify Infected Users
- Better protection, reduced tech support
- Fast updates
- Low costs
Available From:

SPAMHAUS DNS FIREWALL

SURBL BV DNS RPZ
Start your free trial.
Design the best set of data feeds to meet your needs!
Experience improved cybersecurity and stop phishing emails, ransomware, malware, and other cyber threats. Sign up for your free consultation and receive an in-depth technical deep dive and a 30-day free trial.




